
我的荣耀 开启荣耀之旅
By clicking AGREE, you indicate that you accept the HONOR PLATFORM TERMS OF USE.
Keep up to date with Honor products, services and discounts via email.
For further details about withdrawing your consent, please see HONOR Platform Privacy Statement.
- Overview
- Functions and Features
- Privacy Policy
- Feedback on privacy issues
- Overview
- Functions and Features
- Privacy Policy
- Feedback on privacy issues

Owner Identification
This feature helps identify the device owner across devices. When enabled, the facial information stored on the phone will be securely transferred to other devices logged into the same HONOR ID for encryption and local storage, and will not be uploaded to the cloud.

"Extract text" allows you to extract text from an image, then you can copy, drag or tap it to get related services. This service needs to use the text recognition function of HONOR AIEngine to analyze and identify text in images.
"Scan document" takes pictures of your documents via camera with your permission, and crops them for convenient viewing in work, study, and daily life. You can also edit document pictures and save the edited version as an electronic file. With permission to access your photos, you can edit documents scanned and saved to Gallery. This service needs to use the edge detection function of HONOR AIEngine to process your image data.


Bluetooth Tags


Identification

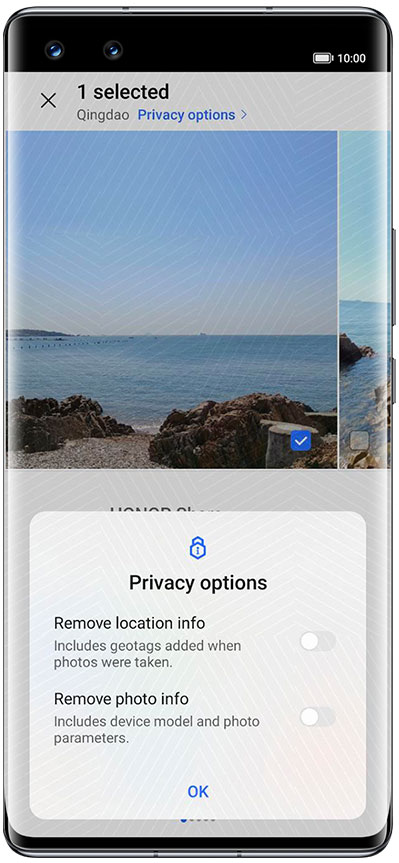
1. You can choose to remove the location and parameter details from image files before sharing them to prevent sensitive information from being revealed.
2. Help protect your privacy by providing the ability to "Remove location information" and "Remove photo information" when sharing pictures.

1. With your authorization, YOYO Suggestions collects app usage information and the pseudonymized device identifier from your device and shares them with third-party travel service providers to obtain your travel information.
2. YOYO Suggestions call HONOR AIEngine to provide proactive services. The data collected for such services will be processed locally on your device. You can turn off HONOR AIEngine at any time in Settings. To enhance HONOR AIEngine, we will anonymize your data and then upload it to our servers. Such data cannot be linked to you. You can disable this function by turning off the User Experience Improvement Program in HONOR AIEngine at any time.
3. When you enter the address, YOYO Suggestions will obtain information about the corresponding location with your permission to provide better travel services. The location information is only processed locally on the device and not uploaded to the server.
4. YOYO Suggestions provide a control switch for each one of their services. You can turn the service on or off at any time according to your needs.



1. The system will provide suggestions on granting the least number of permissions to common apps.
2. Background access to the camera and microphone is not permitted by default.
3. Granted permissions will be automatically revoked for apps that have not been used for 90 days.
granting model

1. A permission can have the following four states: “deny”, “Allow this time only”, “Allow only while in use”, and “Allow all the time”.
2. The Storage permission can have the following three states: “deny” (only access to the app‘s own directories are allowed), “Photo and videos", and "All files".
3. The Location permission will be first granted as "Allow only while in use" and then as " Allow all the time".
access alerts

risk report


launch management

The launch behaviors (self-launch, associated launch or background activity) of individual apps can be managed to restrict unauthorized auto-launches and reduce the risk of revealing personal information. Unnecessary auto-launches can also be restricted using intelligent app launch management, which automatically identifies apps and usage scenarios.
the clipboard

1. Entered lock screen passwords will be stored by an irreversible algorithm and protected with a hardware-bound unique key.
2. Lock screen password verifications are done in a secure and hardware-isolated environment.
3. Magic UI imposes password attempt limits to prevent forced cracking.
The lock screen password must be entered after a reboot or after 72 hours of the last password input and cannot be substituted by biometric authentication methods such as facial recognition and fingerprints.
The lock screen password is also used to encrypt and protect your privacy. Data such as pictures, text messages, emails, and other application data will not be accessible without password verification.

1. The acquisition, detection, extraction, comparison, and storage of facial data are performed in a TEE secure environment.
2. System and the third-party apps that use face recognition will only get the verification result but not the facial data itself.
3. Facial data is encrypted by a high-strength algorithm and saved to a secure storage location.
4. Facial data will only be stored on-device and will not be sent, exported, or backed up to cloud services or external storage media.

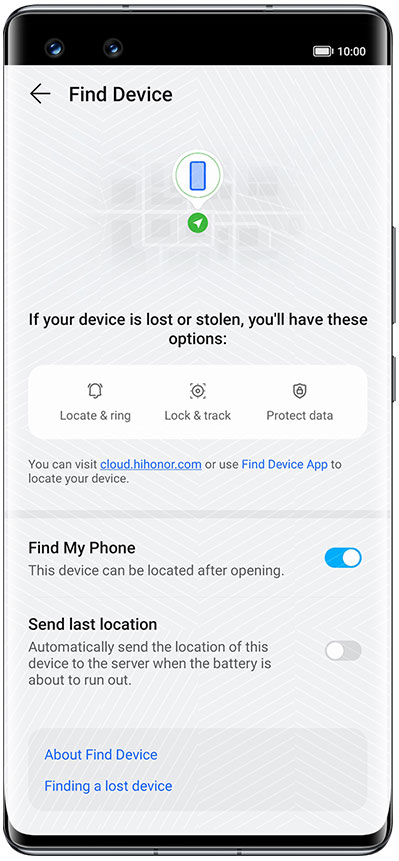
√ Locate device: Shows the location of the device on the map. It includes active positioning and automatic reporting of location information when the battery is low.
√ Play ringtone: The device plays the alert ringtone at maximum volume, regardless of whether it is silent or in vibration mode.
√ Shutdown verification password: After this function is turned on, the lock screen password will be required to shut down the phone.
√ Enable mobile data remotely: If your device is disconnected from the internet when you use Find Device, Find Device will help you remotely turn on the mobile data of your device.
√ Lost mode: Lock the screen and enter a special power-saving mode. Display the message and contact number on the screen and report locations automatically. Send a text message after the internet connection is established. In addition, the contact information on incoming calls and new messages will be hidden.
√ Lock the SIM card: After entering the lost mode, you can lock the SIM card on the device. After that, you need to enter the password when inserting the SIM card into other devices or after restarting the device.
√ Erase data: Restore the device to factory settings and erase all data (including data on the memory card) permanently. After that, you will still be able to locate the device. Your HONOR ID password is still required to use the device.
√ Activation lock: If the device is lost and the data is erased, the next time it is restarted, the user will need to log in to the HONOR ID to re-activate the device. This feature ensures that unauthorized users cannot activate and use the device to keep it safe.
Honor phones equipped with the independent secure chip ensure the security of hardware and information data. The phone is bound to the security chip. Even if lost and maliciously rooted, the HONOR ID password will be required to access the phone. Internal data is encrypted by the secure chip and cannot be accessed even if the ROM chip is physically dismantled.
We use an industry-recognized and certified built-in chip to replace the second-generation U-shield, turning the traditional plug-and-play U-shield into a portable mobile shield that provides financial-grade hardware protection for electronic payments.
-The information shown on this website (privacy protection features and product privacy features) is for reference only. Please refer to the features provided in the product for accurate information. Some features may only be available in certain countries or regions.
-The information shown on this website only applies to the Honor Magic UI mobile systems and certain applications. Please refer to relevant descriptions for the privacy features and functions of other Honor products (such as PC, Tablet, and TV).
-The information shown on this website applies to Honor phones with Magic UI 5.0 and above. Some content applies to Magic UI 3.0 and Magic UI 4.0.
If you have questions or suggestions about the information shown on this site, please click here to contact us.
Subscribe To Our Newsletter - Discover HONOR
By entering your email address, you agree to receive the latest offers and information on HONOR products, events and services. You can unsubscribe from email by entering the link in email messages. You hereby consent to share or transfer your email address to our third-party subscribe service provider located in Hong Kong.
Copyright © Honor Device Co., Ltd. 2020-2024. All rights reserved.
We use cookies and similar technologies to make our website work efficiently, as well as to analyze our website traffic and for advertising purposes.
By clicking on "Accept all cookies" you allow the storage of cookies on your device. For more information, take a look at our Cookie Policy.
Functional cookies are used to improve functionality and personalization, such as when playing videos or during live chats.
Analytical cookies provide information on how this site is used. This improves the user experience. The data collected is aggregated and made anonymous.
Advertising cookies provide information about user interactions with HONOR content. This helps us better understand the effectiveness of the content of our emails and our website.














