

our priority
protection philosophy
provide. From initial design to final delivery, we put privacy considerations into every step and give users autonomous control
over their personal information.
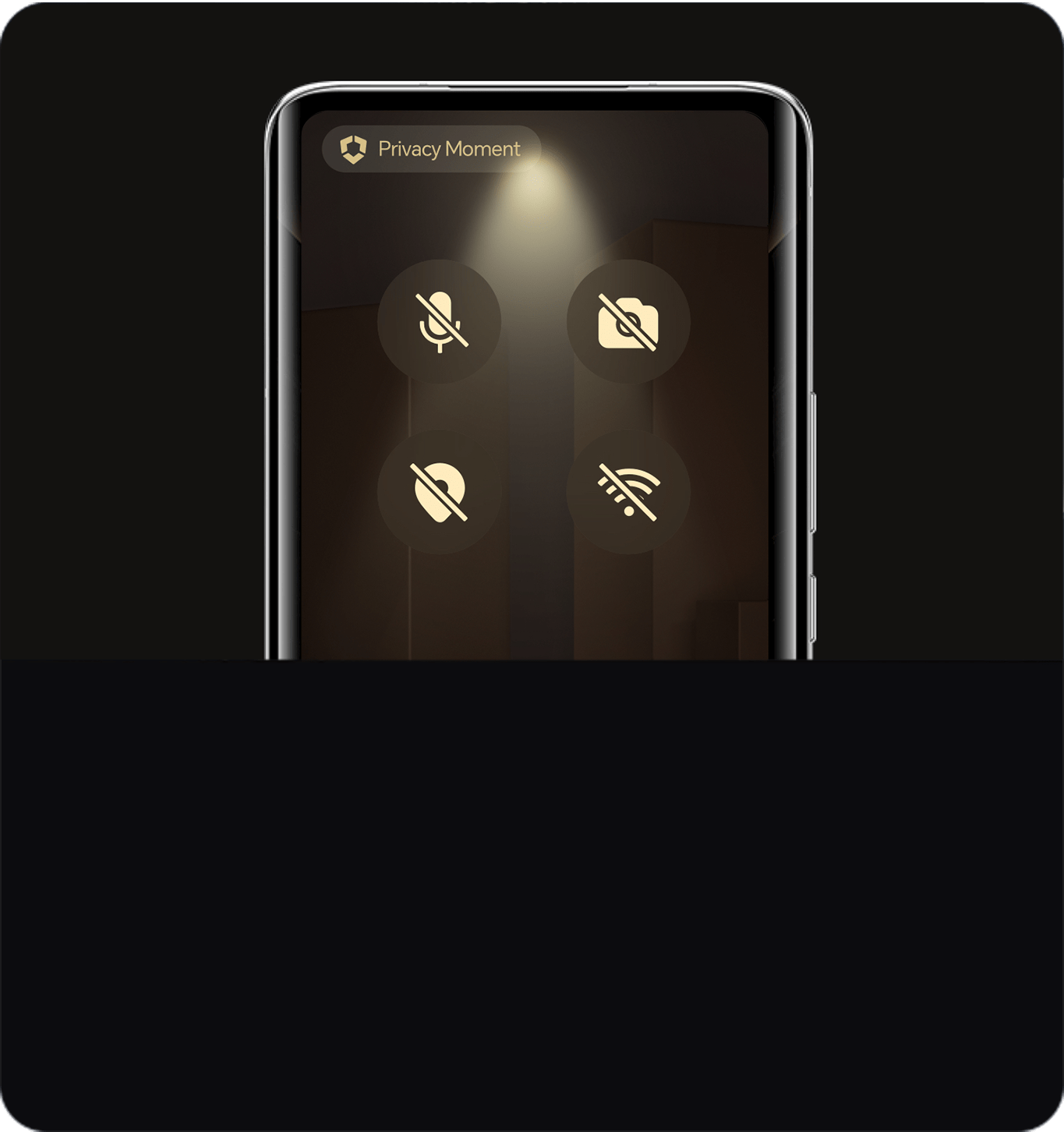



following five aspects of privacy protection




being tracked




system safeguards your privacy at all times.
-The information shown on this website (privacy protection features and product privacy features) is for reference only. Please refer to the features provided in the product for accurate information. Some features may only be available in certain countries or regions.
-The information shown on this website only applies to the HONOR Magic UI mobile systems and certain applications. Please refer to relevant descriptions for the privacy features and functions of other HONOR products (such as PC, Tablet, and TV).
-The information shown on this website applies to HONOR phones with Magic UI 5.0 and above. Some content applies to Magic UI 3.0 and Magic UI 4.0.
If you have questions or suggestions about the information shown on this site, please click here to contact us.




























